Overview

This overview will cover the following areas:
- Why is cyber security important?
- Cyber risk management
- Next steps if a cyber breach is identified
- Additional resources
- Training, CPD and webinars
a) Why is cyber security important?
With the increasing threat, volume and sophistication of attacks, cybercrime is a serious and strategic risk for management and boards.
Heightened geopolitical tensions and remote working have enhanced cyber risks. Higher awareness and expertise is needed to manage cyber security effectively. Cyber threats and attacks may include ransomware, email account take over and monies being paid to fraudsters, but there are many others.
Initially, criminals find a way into your business through the gaps in your defences (these are known as vulnerabilities). Once they get in, they are willing to be patient, watching email exchanges, waiting for the right transaction to divert, or running some ransomware to disrupt your operations.
Methods of attack are constantly changing (as may your technology and the way you work) and are becoming increasingly sophisticated. Your defences need to evolve to keep you protected. It’s an ongoing process that requires periodic reviews and arrangements for assessing that the defensive configurations, policies and controls you have in place continue to be right to protect your firm and ensure they are working effectively.
Top 5 cyber vulnerabilities to accountants:
1) Phishing attacks.
2) Unsecure remote workspaces.
3) Insecure and poorly configured cloud email accounts.
4) Inconsistent cyber and security training.
5) Supply chain weaknesses.
Cyber security is no longer just for the IT team, it is a board priority which should be amongst the top risks on the business risk register. Cyber risks and breaches are applicable to all organisations, regardless of size. Where audit committees exists, they may wish to scrutinise arrangements to obtain assurance over the management and control of cyber security and information risk.
Risk exposure is not just through IT systems or the accounts; operational systems can be a back door. These are varied and may include factory, production, products, emails, website, logistics and physical security breaches such as obtaining false ID allowing unauthorised persons onto company premises who can access company systems.
Human error is an important risk as individuals are often the first line of defence. Security failings can be significant. Ongoing education and periodic test emails to help employees recognise and avoid falling prey to threats is essential.
The cost and scale of managing the risk and response can be bigger than expected. Sometimes this may require specialist recruitment or service providers to support the company.
ICAS has partnered with Mitigo Group to offer cybersecurity risk management services, and exclusive discounts are available for Evolve members.
b) Cyber risk management
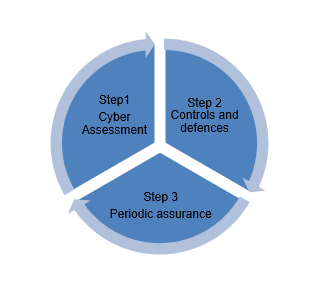
You must undertake a cyber risk assessment to work out your vulnerabilities. Once identified you can put the necessary controls and defences in place. This is a continual process as the criminals are always findings new vulnerabilities to attack.
Step 1: Cyber assessment
- A vulnerability assessment (VA) will help you assess your current risk. This should be conducted by a cybersecurity expert and tailored to your business. A proper VA should include audit interviews, vulnerability scans, application configuration checks, cloud security assessments and penetration testing techniques. This process will identify where your biggest risks are and justify your cyber security concerns.
Step 2: Controls and defences
- You need to ensure your technology is safe and secure. Review the vulnerability assessment with a cyber security expert and your technology partner. This should prioritise the vulnerabilities that are actively being exploited by criminals. It is important to log and track these changes to ensure timely closure.
- Consider getting a cyber security expert to conduct third party interviews to understand the security posture of your supply chain.
- Undertake cyber awareness training to make your staff cyber-competent (they are your most exploitable security weakness). Schedule simulated attacks to help improve your security culture.
- Write and implement policies and processes. This requires you to understand your business – to establish the right policies, processes, guidance and controls to make sure that your security systems keep working, are legally compliant, up-to-date, that people know what to do in what circumstances and the actions to take.
Step 3: Periodic assessment
- Ongoing testing, assurance and support will keep you cybersecure. Have an expert carry out cyber security control checks, launch random attacks and scan to test your vulnerability on an ongoing basis.
- Automated checks and scans will keep your security controls operating effectively, alongside 6 monthly assurance checks which will confirm your security framework is in good working order.
c) Next steps if a cyber breach is identified
First step for CAs – contact the Mitigo cyber breach emergency hotline for CAs if you have either suffered or suspect you may have suffered, a cybersecurity incident. You will need to act quickly.
Our cyber risk management partner Mitigo provides a rapid response, containment, and investigation service. They can assist you with reporting obligations to regulators including the Information Commissioner’s Office (with regards personal data breaches under GDPR), to ICAS and to your clients.
Other examples of cyber incident response forms are in additional resources.
d) Additional resources
For further information on the 3 steps above to help you understand and start cyber risk management and resilience see resources. We encourage you to refer to specialist cyber security support and advice.
- The NCSC board toolkit is a key source for directors overseeing cyber security providing questions for boards to encourage discussion. It has tailored guidance for large organisations, SMEs, public sector and technical experts.
- NSCS briefing packs offer 3 packs to introduce cyber security to your organisation. They have been tailored for large, SME organisations and technical experts. They also provide a small business guide and small charity guide.
- SMEs – risk management: cyber risk and resilience checklist for accountants.
- You can seek certification under the Cyber Essentials scheme. But bear in mind that it only covers the basic principles of cybersecurity, and is therefore not adequate to provide full cyber protection. Real cybersecurity requires a much wider approach to assessing your technical and other aspects of security.
External articles from ICAS partners provide tips and advice on topics such as:
- Password security
- Cyber and data security
- Resilience and ransomware attacks
- Where to focus your cyber security
- Cyber essentials certification
- Cyber threats inside the organisation.
Financial reporting:
- The Institute of Singapore Chartered Accountants have published cyber security considerations in financial statements audit.
- A limited review of annual reports in Cyber and data security disclosures in annual reports finds that whilst cyber risks are commonly identified as principal risks, disclosures of measures to mitigate these risks are highly variable.
Other examples of cyber incident response forms:
- NCSC cyber incident response scheme - organisations who have networks of national significance can use Cyber Incident Response (CIR) certified companies to help them deal with targeted attacks.
- Cyber Scotland incident response explains good practice to have a Cyber Incident Response Plan setting out the steps your organisation should take to prevent, detect, respond and recover from cyber attacks. This should clarify the roles and responsibilities of key individuals who can take action. The plan should be woven into the wider organisational resilience, business and service continuity / disaster recovery planning.
Public sector specific resources:
- The NSCS public sector toolkit
- The Cyber and information security: Good practice guide (NAO) helps audit committees to understand and question the management of cyber security and information risk. This aligns with the UK government’s Cyber Security Strategy aimed at building a cyber resilient public sector.
- For public sector bodies in Scotland, the Scottish Government Cyber resilience: framework and self-assessment tool helps organisations to strengthen the effectiveness of cyber resilience arrangements
- The CyberScotland Partnership website is a one stop shop for cyber advice and guidance.