Where to focus your cyber security – the sequel

We promised you more ‘top tips’ in our last article on how to make your firm cyber resilient. And here they are!
This is one of a series of articles from our Commercial partners. The views expressed are those of the authors and not necessarily those of ICAS.
Five [more] key areas to boost your cyber resilience
Device Lock
To remain secure and GDPR compliant, lock your laptop or desktop when you leave your screen whether you’re working in the office or at home. On Windows hit the Windows key + L on your keyboard. On a Mac press Control + Command + Q. You can also set your screen to automatically lock after a very short time of inactivity.
This is just as important for mobile devices that access corporate information. Always secure your device with a screenlock. A screenlock can be a PIN, password, biometric (fingerprint or FaceID) or pattern. Pick any one of these that you can stick with – some are better than others security-wise, but any is better than none.
Administrator Accounts
As a security best practice, use your local (non-Administrator) account to sign in and then use Run as administrator to accomplish tasks that require a higher level of rights than a standard user account. Do not use the Administrator account to sign in to your computer unless it is entirely necessary. Everyday tasks should not be performed while logged into your computer with the local admin rights. If the machine was to become compromised, this would allow the hacker to run malicious software. There are relatively few tasks that require administrator privileges, such as additional software download for example, so why risk it!
Security breaches of a Microsoft 365 subscription, including information harvesting and phishing attacks, are typically done by compromising the credentials of a Microsoft 365 global administrator account. To protect your global administrator accounts, create dedicated admin accounts and use them only when necessary. Configure multi-factor authentication for your dedicated Microsoft 365 global administrator accounts and use the strongest form of secondary authentication.
Encryption
When working with or sending sensitive information, it’s standard practice to take advantage of the encryption tools already built into the systems you are using. Both data held on your device and data in transit can be encrypted.
If you were to leave your laptop on a train (if you remember what they are) you’d feel less anxious if you knew the data that’s stored on the device was encrypted. Thankfully, up-to-date Apple and Microsoft devices have built-in encryption tools. This secures the data on your disk by encrypting its contents automatically, requiring a password or key to unencrypt the data.
- On a Mac the tool is called FileVault
- On a Windows 10 Pro device the tool is called BitLocker
For data in transit, when sending sensitive information such as payroll reports, email message encryption helps ensure that only intended recipients can view message content. One of the solutions available, Microsoft 365 Business Premium, allows you to control access to sensitive information in emails and documents, with controls like "Do not forward" and "Do not copy." You can also classify sensitive information as "Confidential" and specify how classified information can be shared outside and inside the business. This enterprise-grade encryption is easy to apply to email and documents to keep your information private, allowing your firm to send and receive encrypted email messages between people inside and outside your organisation. It works with Outlook.com, Yahoo!, Gmail, and other email services.
Depending on the email service used by the recipient, they may see an initial alert about the item’s restricted permissions but view the message like any other. Otherwise, they may get a link that lets them sign in to read the email password or request a one-time passcode. If users aren't receiving the email, have them check their Spam or Junk folder.
Home Working
The current COVID-19 lockdown measures mean that everyone must - for now - work from home where they can. Being in the more relaxed home environment, employees may be more inclined to let their guard down when it comes to security. This is when cyber criminals attack, whether it’s fake emails about getting the vaccine or bogus emails asking to pay a supplier, when your colleague isn’t easily contactable to verify the transaction. Keep reminding everyone to stay vigilant while supporting them through this difficult time.
For a variety of reasons, employees may also be using their personal devices to access corporate information. The risk with using home devices is not being on the latest security updates and saving corporate data to personal hard drives. If the device was to fail or a file be deleted, the chances are this wouldn’t be backed up. A solution to this is Microsoft Remote Desktop Services, whereby the user can take control of a remote computer or virtual machine over a network connection to enable them to work as they would in the office. That means all work will be backed up on the corporate network as normal.
An astonishing 1 in 3 companies report losing data stored in cloud-based applications
Office-based employees are usually protected by a firewall and traditional antivirus. To enhance security while working remotely, Lugo include technology such as Endpoint Detection & Response and Cloud Security in their support package. Staff need to be protected even if their network traffic is going directly to the internet. These advanced technologies provide the first line of defence against threats on the internet, wherever users go. It is a fast and easy way to protect all of your users in minutes.
Now is also the perfect time to utilise Microsoft OneDrive or SharePoint, where your team can collaborate remotely on files, meaning no more emailing different versions of spreadsheets or documents. However, many organisations mistakenly believe that Microsoft 365 data is automatically backed up. An astonishing 1 in 3 companies report losing data stored in cloud-based applications, so it may be worth considering a SaaS Backup solution. Users remain the biggest risk to your company data, no more so than at the moment, when it’s being accessed from more locations than usual.
Business continuity planning
Your business continuity plan should be linked to your disaster recovery, incident response and crisis management plans, and supported with the relevant capabilities. These come into play when an incident is serious enough to cause major disruption and/or damage to your business. As identified by the National Institute of Standards & Technology (NIST), the life cycle is: Identify, Protect, Detect, Respond, Recover.
If the worst was to happen, could you be sure your business could continue? For example, if ransomware got hold of your payroll data, would you be confident you could get up and running in time to manage all your clients’ payroll runs without handing thousands of pounds over to cyber criminals? If the answer is not an immediate ‘Yes’ then you need to review (or create!) your business continuity plan.
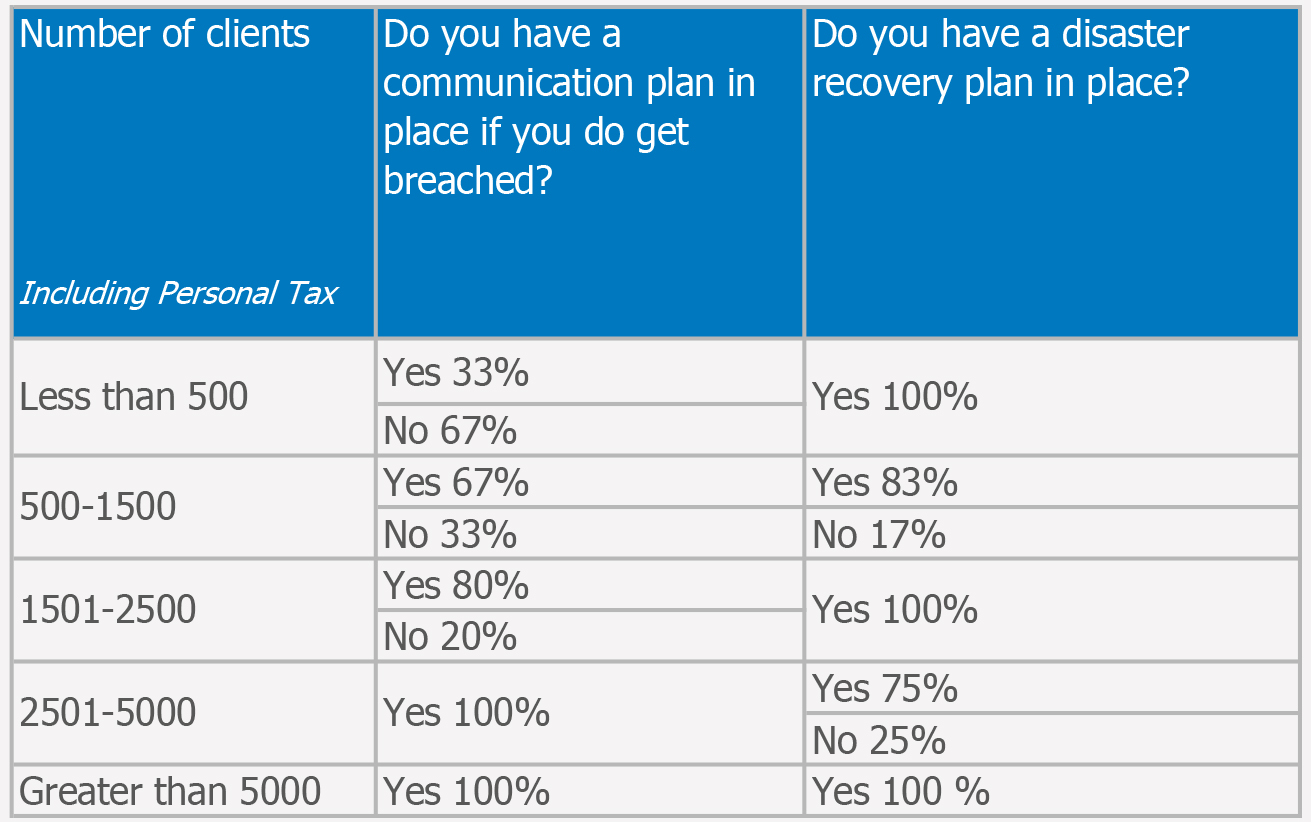
A well planned and executed response will help to minimise the damage caused by a cyber attack. This could mean anything from cutting the amount of data lost, to minimising public and media fall out. We will cover this subject in more depth in a future article, but in the meantime, ensuring all vital business data is backed up is a good first step.
If you have backups of your data that you can quickly recover, you can't be blackmailed by ransomware attacks. There have been a number of ransomware incidents lately where the victims had backed up their essential data (which is great), but all the backups were online at the time of the incident (not so great). It meant the backups were also encrypted and ransomed together with the rest of the victim's data. Whether it's on a USB stick, on a separate drive or a separate computer, access to data backups should be restricted so that they are not accessible by staff and are not permanently connected (either physically or over a local network) to the device holding the original copy.
Outrunning the bear
It can be daunting when there are so many ways your systems and data can become compromised. If you are doing something to protect your systems, you’re doing more than someone who has their head in the sand. Criminals will always go for the low hanging fruit, so the more you do to protect your firm, the less likely you are that you will fall victim to an attack.
You don’t have to run faster than the bear, you just have to run faster than the guy next to you. Jim Butcher
Look out for more insight into the key themes from Lugo and ICAS research in future ICAS articles. If you would like to discuss any element of this article or enhance your own cyber resilience, please email Liz.Smith@LugoIT.co.uk
References
1 Overview of Lugo’s research conducted on IT in Accountancy published in the last ICAS Technical Bulletin in November 2020 (you can access the article here)
